Cisco Cybersecurity Report: Exploit Kits Down, Email Malware Up
Cisco released its 2017 mid-year cybersecurity report showing some important trends in corporate cybersecurity, including a decline in use of exploit kits, a rise in IoT botnets and destruction of services campaigns, and the return of email spam as an effective attack vector.
Exploit Kits Are Fading Into The Background
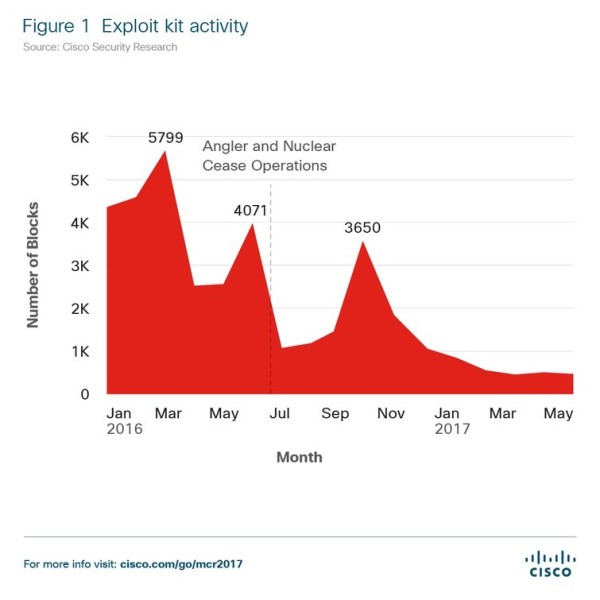
According to Cisco’s cybersecurity report, three of the main exploit kits–Angler, Nuclear, and Neutrino–abruptly vanished from the landscape last year. Neutrino returned eventually, but in the form of a subscription service for attackers, rather than as an exploit kit that’s available as a one-time purchase.
What this “service” means for the landscape is that the attacks are more controlled, so it’s harder to detect, while at the same time giving smaller crime groups a chance to use it, too, for a lower subscription cost. However, Cisco said that the overall exploit kit activity has been declining dramatically since January 2016.
According to the company, reasons for the decline include the arrest of the Angler exploit kit author, as well a faster update cycle for previously more vulnerable software platforms such as Flash, web browsers, and Windows, which gained automatic updates with the launch of Windows 10.
Network security research firm Qualys found that it took companies, on average, 308 days to patch 80% of Flash vulnerabilities in 2014, whereas it took them only 62 days in 2016. Exploit kit developers now find that they have to chain together multiple exploits in order for their attacks to be successful.
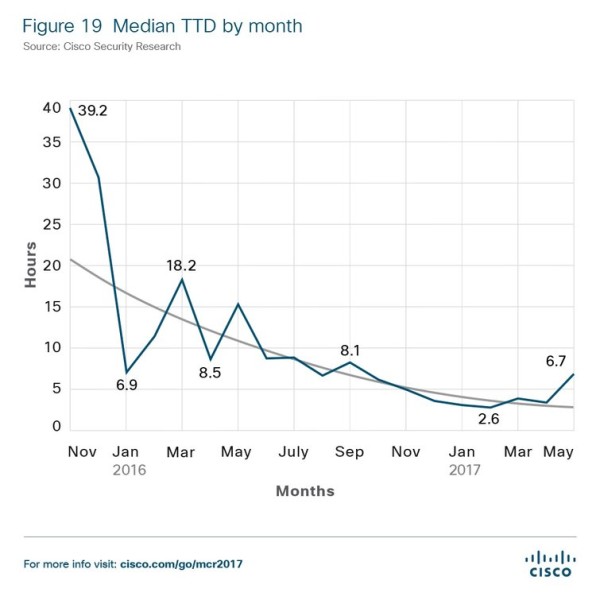
Cisco’s own research also found that the time it takes to detect a data breach inside a company’s network has been reduced from 39 hours in 2015 to about 3.5 hours for the period from November 2016 to May 2017.
However, Cisco warned that companies should remain vigilant. Although the exploit kit landscape may remain dormant for now, the tools have already been created, and they could be re-activated with the appearance of new major vulnerabilities in popular platforms. If companies allow too much time to pass between the discovery of a major vulnerability and fixing it, then the exploit kit market could once again become lucrative.
Email Spam Is Back
As exploit kit activity has decreased, email spam and malware seem to have made a comeback. Malicious hackers use email as a delivery method for their ransomware and other types of malware. The Cisco researchers anticipate that the volume of email spam will continue to rise as the exploit kit landscape remains in flux. Through email, attackers can also gain entrance to more privileged areas of an organization’s network, from which they can do more damage.
According to Cisco, business email compromise (BEC) is the #1 threat in organizations, even though this type of attack is not as high-profile as ransomware attacks tend to be these days. A BEC campaign involves having an attacker request funds from a financial employee using spoofing to appear as if the request is a legitimate one.
Attackers have siphoned $5.3 billion from companies between 2013 and 2016 using this tactic, compared to only $1 billion gained through ransomware in 2016, according to the Internet Crime Complaint Center.
Ransom Denial Of Service (RdOS)
Some cybercriminal groups, such as the Armada Collective, leverage the threat of a DDoS attack to demand a ransom from companies. A “demo” attack usually follows the request to show that they mean business.
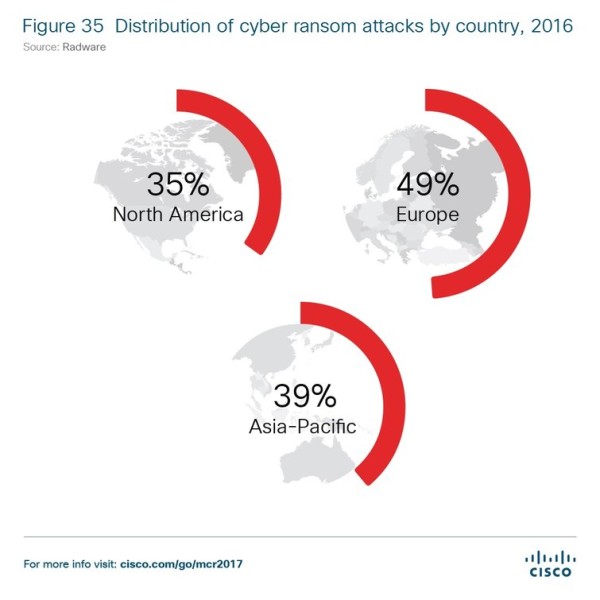 According to Cisco, nearly half (49%) of the researched companies received a ransom note in 2016, a number that seems striking. The Armada Collective typically asks for 20 Bitcoins as ransom, although other groups may ask for less or more.
According to Cisco, nearly half (49%) of the researched companies received a ransom note in 2016, a number that seems striking. The Armada Collective typically asks for 20 Bitcoins as ransom, although other groups may ask for less or more.
Destruction Of Services
Destruction Of Services (DeOS), a term coined by Cisco, seems to be on the rise, as well. Over the past year, Cisco has observed attackers building IoT botnet capabilities that can later be used to disrupt services. We’ve also seen with the recent NotPetya attack that some actors, especially some nation-states, may not be interested in obtaining ransom money, but in destroying or disabling certain infrastructure.
IoT Botnets
As proven last year by the DynDNS attack, as well as other major DDoS attacks, we now seem to be in the age of terabit-per-second DDoS attacks enabled by hundreds of thousands or millions of infected Internet of Things (IoT) devices.
The open source Mirai botnet, as well as the severe lack of security or a proper automatic update mechanism for the vast majority of IoT devices, has led to attack campaigns that can be setup and launched with over 100,000 infected devices within a day.
Cisco recommended the following actions for companies looking to defend themselves against attacks targeting their IoT networks:
- Keep older signatures active
- Surround IoT devices with IPS defenses
- Closely monitor network traffic (this is especially important to do in IIoT environments, where network traffic patterns are very predictable)
- Track how IoT devices are touching the network and interacting with other devices (for example, if an IoT device is scanning another device, that is likely a red flag signaling malicious activity) Implement patches in a timely manner
- Work with vendors that have a product security baseline and issue security advisories
Cybersecurity Has Never Been More Important
Cisco warned that attackers are building tools that can completely disrupt or destroy the operations of a company, because they know the vast majority of firms don’t have a contingency plan for rebuilding their IT infrastructure from scratch in case of a devastating cyber attack. The attackers plan to use this to their advantage, either to obtain larger sums of money as ransom or to further some other objective.
Cisco said that this means companies need to start taking cybersecurity much more seriously and to invest in tools and infrastructure that can keep their networks and data secure. Cisco also argued that security vendors need to work together to develop more interoperable tools that can together meet the challenge of more potent attacks.
“Complexity continues to hinder many organizations’ security efforts,” said David Ulevitch, Senior Vice President and General Manager, Security Business Group, Cisco, in an email to Tom’s Hardware.
“It’s obvious that the years of investing in point products that can’t integrate is creating huge opportunities for attackers who can easily identify overlooked vulnerabilities or gaps in security efforts. To effectively reduce Time to Detection and limit the impact of an attack, the industry must move to a more integrated, architectural approach that increases visibility and manageability, empowering security teams to close gaps,” he recommended.