Researchers Find Screenshot Malware on App Store | Here’s How to Protect Yourself

A new piece of malware has been discovered on the App Store that attempts to steal information from unsuspecting users by scanning their photo libraries for screenshots containing targeted keywords. These are typically related to crypto wallets, suggesting that attackers are looking to specifically compromise those, but it wouldn’t be difficult for the same tools to target anything else.
The malware-laden apps were discovered by Dmitry Kalinin and Sergey Puzan of Kaspersky Lab. The duo published an in-depth look at the malware, which they’ve dubbed “SparkCat.”
The concept behind SparkCat isn’t new, as researchers at ESET discovered similar techniques built into messaging apps in March 2023. Kalinin and Puzan first came upon SparkCat in late 2024, noting that it’s been active since at least March.
The campaign, which targeted Android and Windows users, saw the malware spread through unofficial sources. In late 2024, we discovered a new malware campaign we dubbed “SparkCat”, whose operators used similar tactics while attacking Android and iOS users through both official and unofficial app stores.
Dmitry Kalinin and Sergey Puzan, Kaspersky Lab
While such malware has been common on the Google Play Store for years, the researchers noted that this is the first time an app like this has been found in Apple’s App Store.
To make things even more complicated, it’s unclear if these apps exist specifically to carry SparkCat or if the malicious code has been inserted into the app as part of a third-party SDK. Few developers build everything in their app from scratch; it’s common for them to use third-party SDKs for things like in-app advertising and tracking metrics — code that other developers create for reuse across dozens or hundreds of apps.
In the past, Apple has taken action against apps that secretly gather personal data, but some of this stuff is so well-hidden that it’s hard for the App Store Review team to find it. Six years ago, we shared a report on how the games on your iPhone could be sharing more data on you than even their developers realize, and it’s likely that practice hasn’t stopped.
“Some of the apps, such as food delivery services, appeared to be legitimate,” Kalinin and Puzan note, “whereas others apparently had been built to lure victims.” However, they all have one thing in common: they attempt to trick you into allowing the app to access your photo library.
While an app that can scan your screenshots sounds alarming at first glance, it turns out that it can’t do anything you haven’t given it permission to do. This malware isn’t bypassing the permissions Apple has built into iOS — it’s merely abusing them.
How to Protect Yourself Against SparkCat
First off, the SparkCat malware doesn’t run in the background, so it can’t watch what you’re doing in other apps. Instead, it tries to scan screenshots from your photo library to look for anything of value.
Like any other app, you have to grant it that permission first. Of course, many folks do that blindly, and the cyber crooks here weren’t born yesterday — they’ve deliberately used apps where it doesn’t seem unusual to ask for that permission. AI apps that can analyze and modify pictures seem to be a common example, although the researchers also found a Chinese food delivery app that seems more dubious (I can’t think of any logical reason why I’d need to let Uber Eats or DoorDash access my camera or photo library).
Once you’ve given a SparkCat-laden app access to your photos, it fires up an optical character recognition (OCR) engine to scan your photo library for any screenshots that contain information related to crypto wallets, presumably hoping to gain enough information to compromise your accounts. While SparkCat appears to be targeted at crypto, it wouldn’t be difficult for other crooks to repurpose it to scan for other sensitive info.
The first line of defense against malware like SparkCat is to always be wary of granting unknown apps access to all your photos.
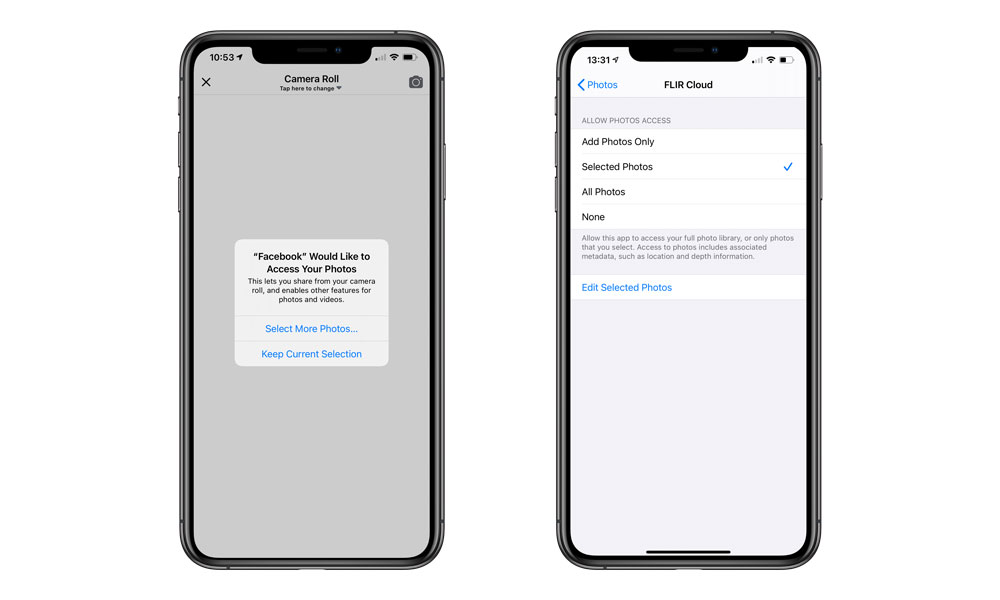
The SparkCat malware can’t touch your photos until you grant permission. If you really want to share some photos, use selective photo sharing instead. This was added in iOS 14 and improved in iOS 17. As the name implies, it lets you share only a few specific photos with the app. If the app has SparkCat hidden inside, that malware will still be able to scan the photos you select, but it won’t be able to see anything else. As far as the app is concerned, those photos comprise your entire photo library.
If you choose to share sensitive photos with selective photo sharing, that’s on you, but this brings us to the second point: avoid storing anything sensitive in your photo library in the first place. If nothing in your photo library contains sensitive information like passwords, recovery keys, or banking information, then malware like SparkCat won’t be able to find anything useful.
That doesn’t mean you shouldn’t be prudent about granting carte blanche access to your photo library to relatively unknown apps. You should be careful even with known apps like Facebook, which is known for spying on its users — and is always looking for more ways to gather data on you.
This is why Apple’s selective sharing feature is so valuable. While it takes a couple of extra steps to authorize a social media app to access the photos you want to share, those additional taps are worth the tradeoff for keeping your personal photos private.