With Tweaks, Edward Snowden’s ‘Haven’ App Helps Track Intruders
Edward Snowden has released an app. If that makes you pause, that’s understandable; you might not consider the NSA leaker and current Russia resident the most trustworthy of individuals at first.
His collaborators on the open-source Android app Haven include the Freedom of the Press Foundation—which Snowden runs—and The Intercept’s Micah Lee, who helped co-found the organization, develop the app, and test it over nine months.
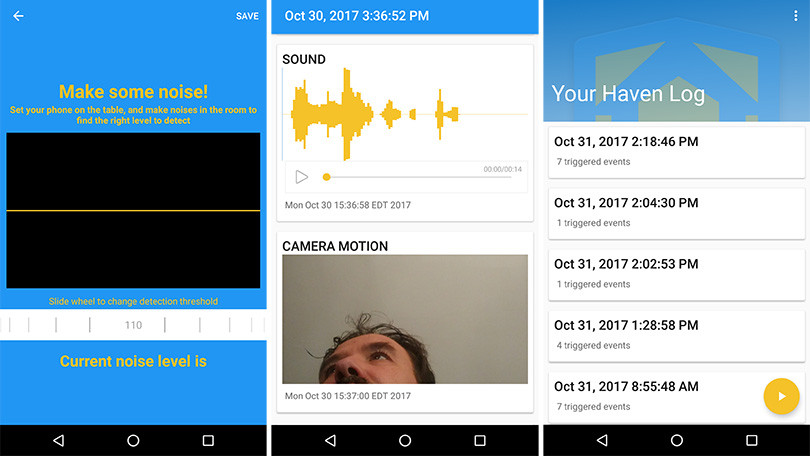
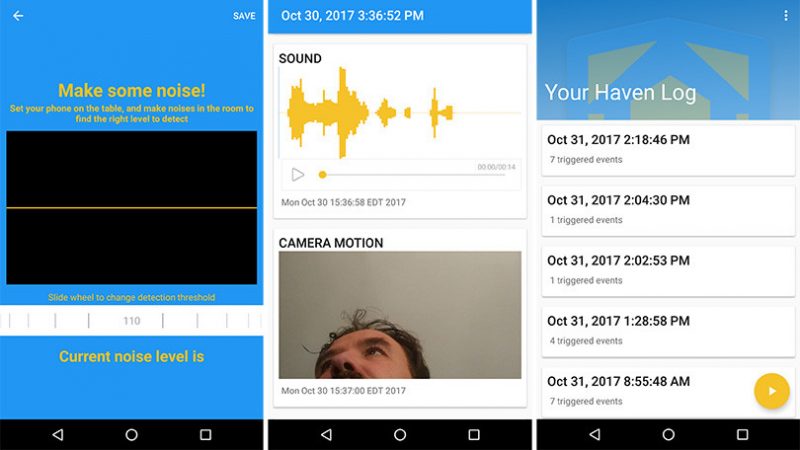
Haven’s premise is simple. If you have a crappy old Android phone that you aren’t using anymore, you can install the app to turn the device into a mega-surveillance machine of sorts. For example, assume you’re on a trip and you’re carrying some important information on your laptop. While it’s probably best if you keep your laptop in sight at all times, there might be moments where you need to leave your laptop in your hotel room. And if you’re the slightest bit paranoid—as you should be—Haven can help you figure out whether anyone snuck into your room and tried to access your device.
“Here’s how Haven might work: You lock your laptop in a hotel safe—not a secure move on its own—and place your Haven phone on top of it. If someone opens the safe while you’re away, the phone’s light meter might detect a change in lighting, its microphone might hear the safe open (and even the attacker’s speak), its accelerometer might detect motion if the attacker moves the laptop, and its camera might even capture a snapshot of the attacker’s face. The Haven app will log all of this evidence locally on the Android device,” Lee writes.
Haven can also notify you whenever it records activity (and send you an image of what it saw). You can elect to receive these messages via a less-secure text message, but Haven can also send out notifications using the messaging app Signal—for end-to-end encryption. You can also use Haven with the Android app Orbot to transform your Android smartphone into a Tor server. You’d still be able to view these notifications and images, but over a service where it’s incredibly difficult to track individual users.
Of course, a truly nefarious intruder can use other ways to get around Haven’s scanning.
A clever attacker who knows that you’re using Haven could jam the wifi, mobile data, and SMS wireless frequencies, preventing Haven from sending you notifications. The attacker could then attempt to access the phone to delete the local evidence logs from the device as well,” Lee writes.