WannaCry Ransomware Lives On (But With Less Bite)

WannaCry is still kicking and looking for its next victim, but it’s not quite the monster it was earlier this year.
The worm-like ransomware remains active because so many unpatched Windows machines are still connected to internet, according to Kryptos Logic, the security firm that helped cripple the outbreak.
The good news is that the new infections have been harmless, and won’t trigger WannaCry to encrypt the system’s files. Back in May when WannaCry first emerged, a researcher with Kryptos Logic famously activated a “kill switch” in the ransomware that effectively sterilized the attack.
Since then, Kryptos Logic has been monitoring the web domain that triggered the kill switch, which continues to tell new WannaCry infections to stand down.
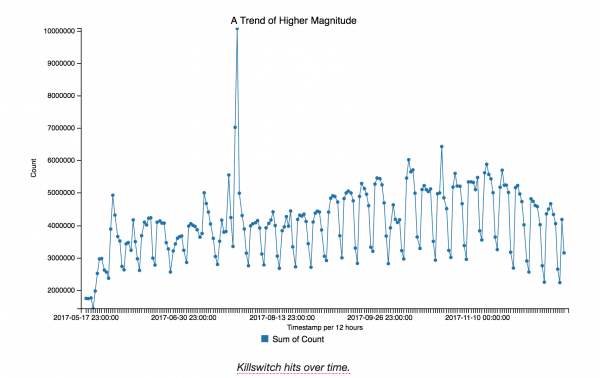
Over the past six months, the traffic to the kill switch has remained quite high. “At the time of this writing, we count approximately 900 million cumulative thwarted attacks across millions of unique IP addresses,” the company said in a Wednesday blog post.
Fortunately, each new infection is running in a “benign state,” Salim Neino, CEO for Kryptos Logic, said in an email. After a reboot, unpatched machines carrying the infection will contact the kill switch again only to remain dormant.
What might be spearheading these new infections? Neino blamed it on computers that were hit with the WannaCry attack before the kill switch went live. These infections would have completely taken over the computer to malicously spread the attack. It’s possible these machines may have been forgotten, and no one bothered to clean them up, Neino said. As a result, they’d have free rein to scan the internet for vulnerable machines to infect.
“Many times the scanners will hit a new system they have not reached before and create a quick outbreak,” Neino said. “In some cases, we see thousands of PCs behind one IP address, which have never been registered before, all of a sudden start to light up months later.”
The persistent WannaCry infections have plenty of targets to hit, Neino added. Microsoft issued a Windows fix that can prevent the WannaCry attack, but many businesses still struggle to patch their computers with the latest software.
The security firm Symantec has also found that the ransomware continues to persist. “Since the day WannaCry appeared, the team has constantly seen WannaCry infection (attempts) which will probably never end,” the company said in an email.
But even as the WannaCry threat has been neutralized, businesses and users should do what they can to patch their systems. Kryptos Logic is warning that a future ransomware outbreak might very well use the same methods as WannaCry to spread, potentially putting millions of unpatched Windows machines at risk.
Earlier this week, the US blamed the WannaCry attack on North Korean state-sponsored hackers, claiming they wanted to create chaos.
Update: Both Symantec and Kryptos Logic explained that there is a scenario where WannaCry can succesfullly infect a computer, despite the kill switch.
This can happen when a Windows PC is infected with WannaCry, but the machine itself has no broad access to the internet and thus no way to contact the kill switch. As a result, a full WannaCry infection will take hold.
Businesses harboring any live WannaCry-infected machines might face this attack scenario.
“For example, imagine in an enterprise environment, there is a machine infected and constantly scanning the LAN (Local Area Network),” Symantec said in an email. Any unpatched Windows PC on the corporate network that has no external internet access will fall victim to a full WannaCry infection.