New 7-Zip Archiver Hack Reveals a Long Ignored Windows Vulnerability
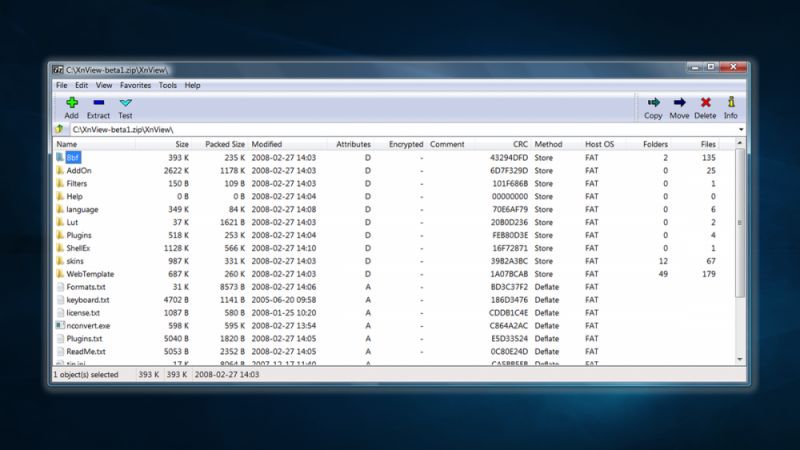
The latest versions of 7-Zip contain a vulnerability (CVE-2022-29072) that lets hackers gain administrative privileges on a system. But this vulnerability, which exploits the 7-Zip help file, should alarm all Windows users, as it highlights an age-old problem on Windows systems.
How Does the Exploit Work?
As you may know, 7-Zip is a pretty old piece of open-source software. Its interface, buttons, and help menu haven’t changed much since 1999. The help menu is especially nostalgic—it relies on a .chm help file, which is a relic from the days of Windows 98.
These old .chm files are pretty versatile. When opened, they can display HTML and Javascript, making them a solid option for e-books, dictionaries, and other documentation. But they’re also easily exploited, as they can run malicious code and effectively substitute for an executable.
Now, 7-Zip’s help file doesn’t contain malware. But as kagancapar explains, hackers can use this file to execute malicious code on your system.
The process here is a bit wonky, so stay with me. Hackers with local or remote access to your computer can drag a .7z archive into the 7-Zip help menu to open a command prompt with admin privileges. The cmd.exe prompt runs as a child process under 7zFM.exe, which is quite odd.
A misconfiguration in the 7z.dll file and heap overflow appear to be responsible for this problem. Normally, dragging a file into the 7-Zip help menu should do nothing. I should note that a similar problem recently affected WinRAR, another archiving tool.
Realistically, the average person won’t be affected by this exploit. It requires local or remote access to your computer, and if a hacker manages to get that far, then you’re already screwed. If you’re worried about this vulnerability, you can simply delete 7zip.chm. It should be under C:/Program Files/7-Zip or C:/Program Files (x86)/7-Zip, depending on whether you use the 64-bit or 32-bit version.
Note that this problem only seems to affect the latest version of 7-Zip (21.07). This particular update launched in December of 2021, and 7-Zip hasn’t confirmed plans to patch the problem.
Sill, escaping from this vulnerability may not save you from future .chm exploits, as Microsoft is partially responsible for such hacks.
Microsoft Needs to Address Old Help Files

By default, Windows tries to open .chm files in the old HTMLHelper, also called hh.exe. This viewer executes HTML and Javascript and provides very little protection from exploits. Hackers are known to use .chm files to run malicious code in HTMLHelper, usually through phishing schemes.
Microsoft has made some lightweight attempts to fight this problem—Outlook no longer opens .chm files, and many .chm files are automatically blocked from running in Windows. But as we see with today’s news, HTMLHelper and .chm files present an ongoing security risk for Windows PCs.
You could blame 7-Zip for leaving bugs in its software, but realistically speaking, a misconfigured .dll file shouldn’t let hackers run malicious code on your computer. The problem lies with Microsoft and its HTMLHelper software.
I suggest avoiding .chm files until Microsoft finds a way to resolve this problem. That said, you shouldn’t uninstall hh.exe, as doing so could negatively impact system performance.
Source: WinFuture